Enterprise Email Security Implementation
Automated quarantine digest, threat intel enrichment, and live KPIs for Microsoft 365.
Automated quarantine digest, threat intel enrichment, and live KPIs for Microsoft 365.
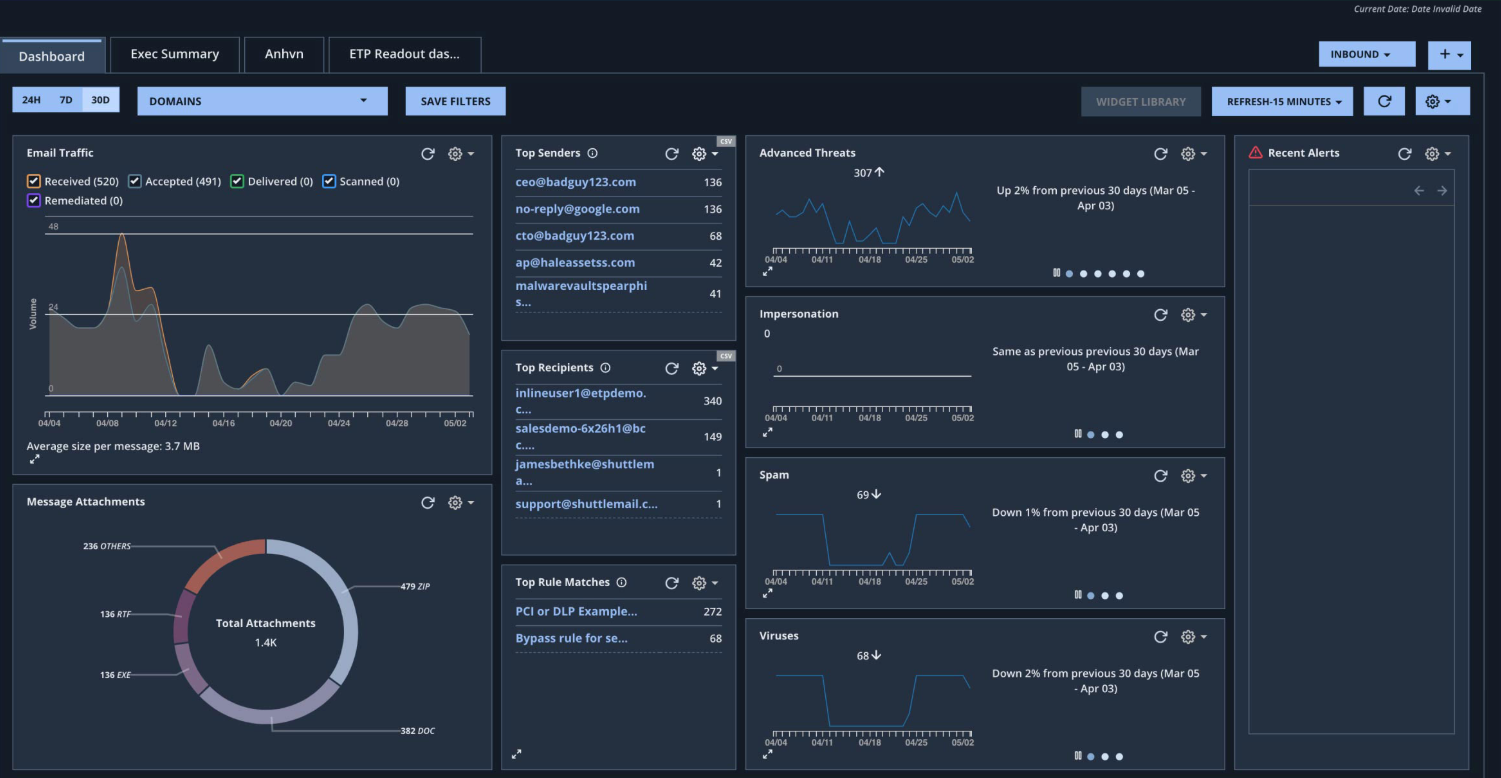
We implemented a secure pipeline that ingests email threat data (spam, phishing, malware), enriches it with sender/IP intelligence, and generates an automated Quarantine Digest for end users and admins. A lightweight HTML dashboard surfaces trends, top senders, and release/keep actions. All actions are logged with correlation IDs for audit.
Pluggable: add VirusTotal/IPQualityScore, SIEM, or custom allow/deny logic.
Microsoft Defender for Office 365 Exchange Online / Graph API Power Automate (flows for ingestion, enrichment, digest build, artifact publish) Optional enrichment via PowerShell/Python Artifacts hosted on GitHub Pages (CSV/JSON)